Cloud: Security
RavenDB cloud products use several layers of security.
-
All instances are encrypted using HTTPS and TLS protocol version 1.2 or 1.3.
-
Servers and client applications authenticate each other using X.509 certificates.
Note that a RavenDB cloud product comes with an initial client certificate.
You need this certificate in order to access your RavenDB instances. -
You can choose which IP addresses your server can be contacted by.
-
Your mandatory backup routines produce encrypted backup files.
-
In this page:
Using The Initial Client Certificate
A client certificate is automatically generated during the creation of your RavenDB cloud product.
You will need to import this certificate to your browser in order to access your cloud instances.
Download Certificate
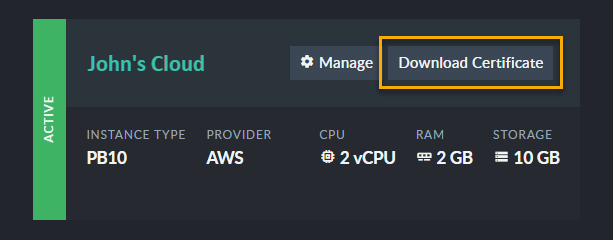
Go to the Products tab in the cloud portal and click the Download Certificate button.
Install the certificate
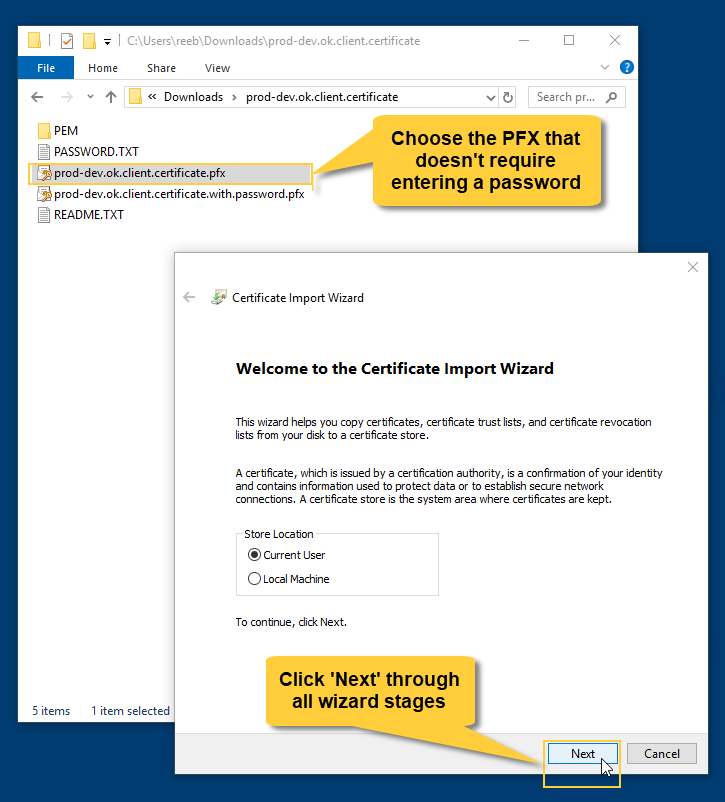
Extract the certificate package, open the extracted files' folder, and double-click the .pfx file that requires no password.
When the certificate import wizard is launched, click "Next" all the way through the wizard.
Access your product
To access your product your IP address must be added to the Allowed IPs list.
Allowed IPs entries are CIDR ranges
that define networks from which the connection is allowed.
- You can set Allowed IPs to
0.0.0.0/0, which would allow access from any location, or you can specify certain IPs or IP ranges. - Be aware that you will not be able to access your instance from locations that are not specified in the allowed IPs list.
- You can edit the list at any time through the Portal.
- Regardless of the allowed IPs setting, your RavenDB Cloud instances will always require authentication using X.509 certificates for access. The allowed IPs list serves as an additional layer of security, but isn't the only one.
Azure products do not permit overlapping of addresses in the Allowed IPs list.
If addresses in your list overlap, an error is going to be displayed upon product creation. E.g. -
- Listing both 13.64.151.161/32 and 13.74.249.156/32 is **not permitted**.
- Listing 0.0.0.0/0 and any other address is **not permitted**.
- Listing both 51.140.148.192/27 and 13.74.249.156/32 **is permitted**.
Cross-instance communication inside the cluster is not subject to these restrictions.
If you're using Chrome on Windows, you will now be able to access your RavenDB cloud instance. You may need to restart your browser.
In other cases (e.g. if you're using Firefox) you will have to import the certificate to your browser manually.
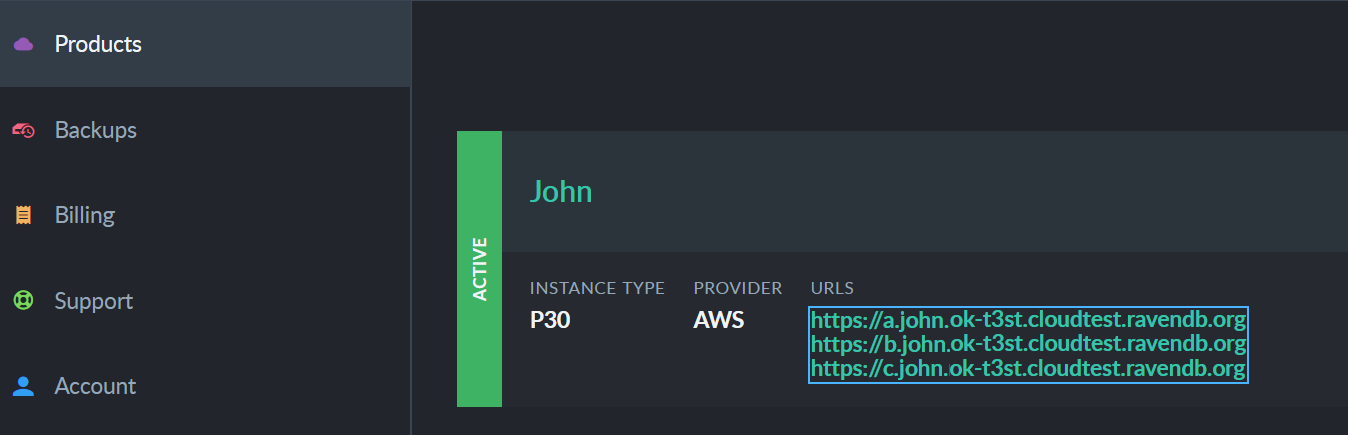
Once the certificate is imported, click your cloud instance's URL.
Your browser will prompt you to select a certificate. When you select the client certificate, your product's
management studio will launch.
Using Additional Certificates
Your initial operator-level
certificate allows you to perform operations like creating and deleting databases, managing access to the cluster, and inspecting the cluster's state.
Operations like adding and removing cluster nodes are left for your products administrators.
We recommend that you generate and use different certificates for your client applications, for maximum security.
If your instance runs on a burstable CPU, especially if it is a low-end one,
RavenDB may take a while to generate certificates and spend a lot of your CPU credits in the
process.
We therefore recommend that you generate your certificates off-cloud and import them to your cloud instance.
To generate additional operator or user certificates:
- Go to the server management studio, and click the
Manage Certificatesbutton.
- Click Generate client certificate