Certificates Management View
-
The built-in RavenDB Studio enables full customization of client certificates as well as importing and exporting of certificates.
-
This article gives brief guidance about the Studio certificate management GUI.
For detailed explanations including the RavenDB Security Authorization Approach, see the article Certificate Management.
In this page:
- Certificates Management Studio View
- Configuring Certificates: Database and Access Permissions
- Enabling Communication Between Servers: Importing and Exporting Certificates
Studio Certificates Management View
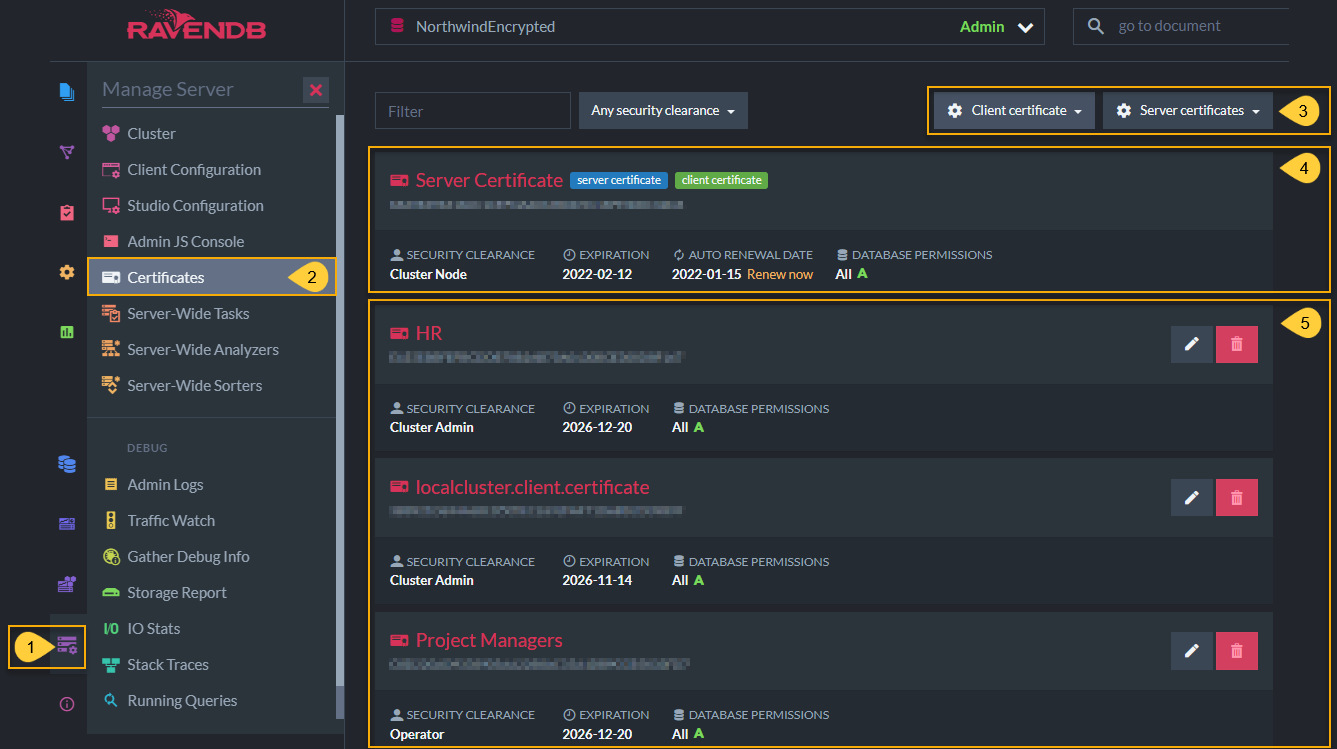
Studio Certificates Management View
- Click Manage Server tab.
- Select Certificates.
-
Client certificate
- Generate and configure a new client certificate
- Upload a client certificate that was exported from another server so that they can communicate.
-
Server certificates
- Export server certificates so that you can import them into another server.
- Replace server certificates by uploading another
.pfxcertificate.
- Status of current server certificate. You can click Renew now here.
- Status of current client certificates active in this server. You can remove or edit client certificates, including configuring databases permissions and authorization (security clearance) levels here.
Client certificates are managed by RavenDB directly and not through any PKI infrastructure. If you want to remove or reduce the permissions on a certificate handed to a client, you can edit the permissions or remove them entirely in this Studio screen.
Configuring Certificates: Database and Access Permissions
In the image below, the client certificates (HR, localcluster.client.certificate, Project Managers) have different security clearance and database permissions configurations.
This is done to give admins the ability to protect the contents of their databases by customizing permissions.
For example, if an application user should have read/write but not admin access over the HR database, while project managers should have operator permissions on all databases, you can grant different access levels by using different client certificates, each with its own set of permissions.
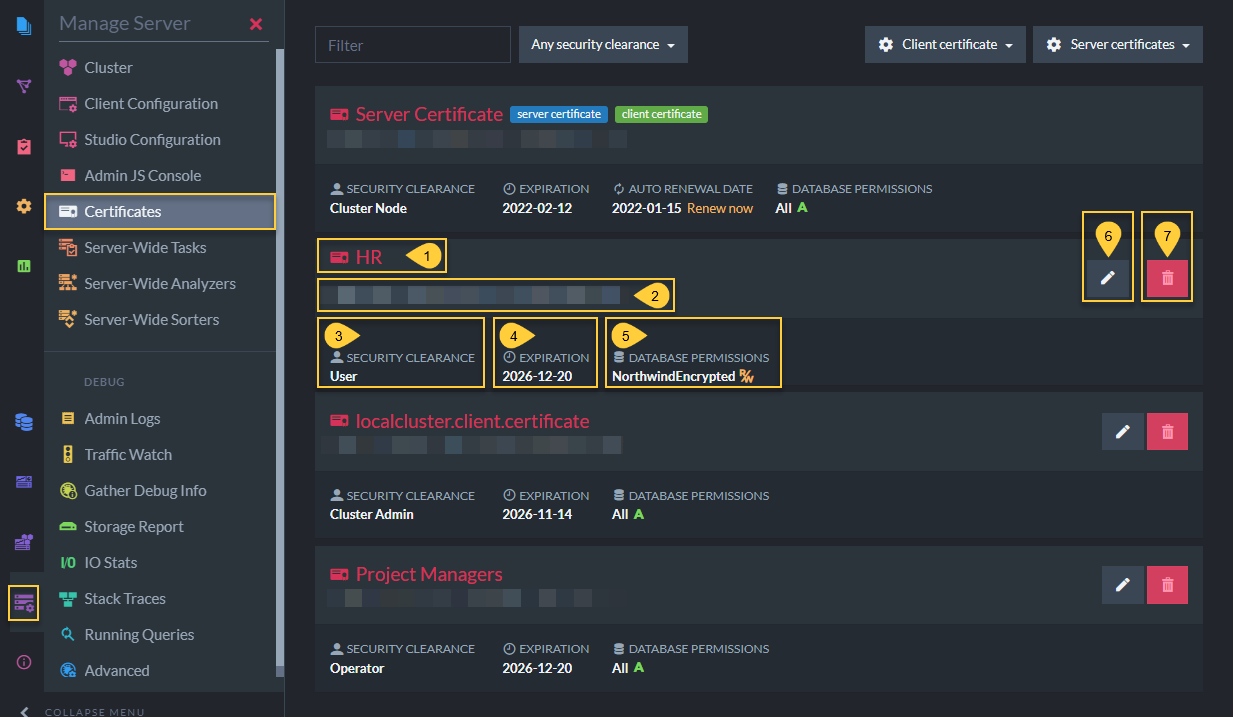
Status of Registered Certificates
Each client certificate contains the following:
- Name
Client certificate name. - Thumbprint
Unique key for each certificate. - Security Clearance
Authorization level that determines types of actions that can be done with this certificate. - Expiration date
Client certificates are given 5 year expiration periods by default. - Allowed Databases
The databases in this cluster that this client certificate has access to. - Edit Certificate
Configure which databases it can access (applicable for User level) and its authorization clearance level. - Delete Certificate
Generate Client Certificate
Using this view, you can generate client certificates directly via RavenDB.
Newly generated certificates will be added to the list of registered certificates.
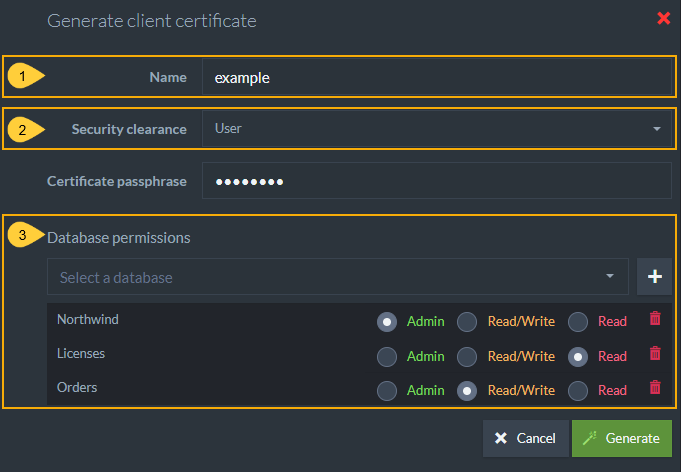
Generate Client Certificate
When generating a certificate, you must complete the following fields:
- Name
- Security Clearance level
-
Allowed databases and access level for each database.
- If you choose User security clearance, you can give access to specific databases on the server and configure User authorization levels for this certificate.
This information is used by RavenDB internally and is not stored in the certificate itself.
Expiration for client certificates is set to 5 years by default.
Edit Certificate
Every certificate in the list can be edited. The editable fields are:
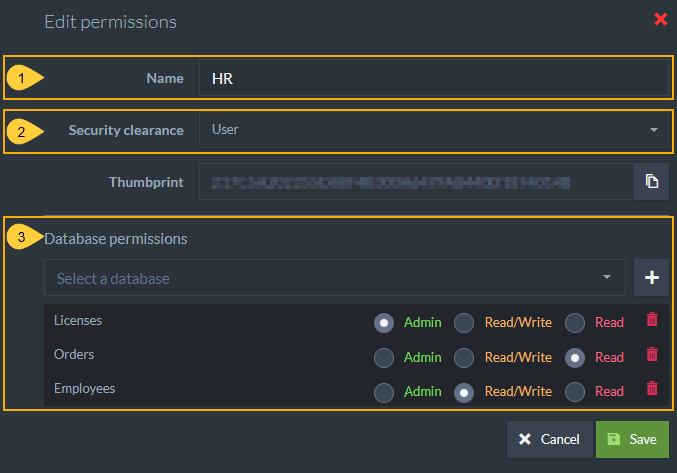
Edit Certificate
- Name
- Security Clearance level
-
Allowed databases and access level for each database
- If you choose User security clearance, you can give access to specific databases on the server and configure User authorization levels for this certificate.
This information is used by RavenDB internally and is not stored in the certificate itself.
Enabling Communication Between Servers: Importing and Exporting Certificates
Upload an Existing Certificate
Using this view you can upload existing client certificates.
Uploaded certificates will be added to the list of registered certificates.
To connect two secure databases, you must
a. Export (download) the .pfx certificate from the destination cluster.
b. Upload (import) the downloaded certificate into the source server.
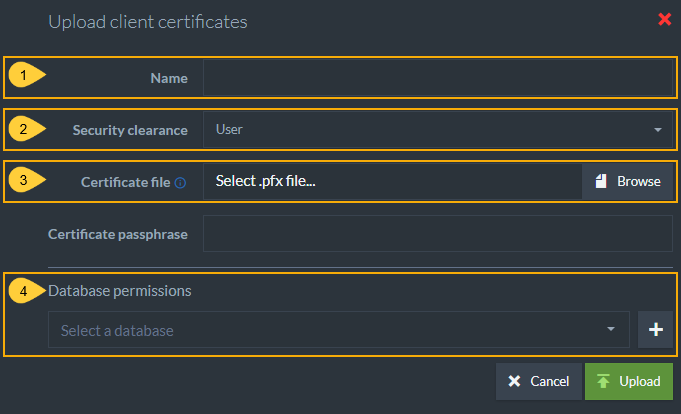
Upload Existing Certificate
When uploading an existing certificate file, you must complete the following fields:
- Name
- Security Clearance level
- Upload the
.pfxcertificate file from the destination server installation folder. -
Select databases and permission levels
- If you choose User security clearance, you can give access to specific databases on the server and configure User authorization levels for this certificate.
This information is used by RavenDB internally and is not stored in the certificate itself.
Export Server Certificates
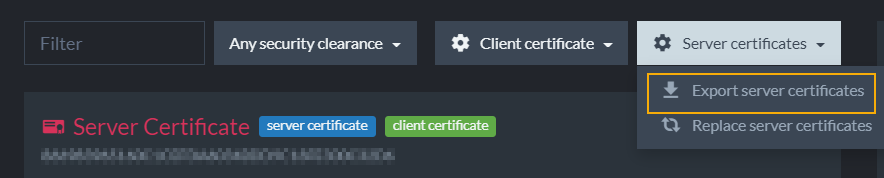
Export Server Certificates
This option allows you to export the server certificate as a .pfx file. In the case of a cluster which contains several different server certificates, a .pfx collection will be exported.
Certificate Collections
Pfx files may contain a single certificate or a collection of certificates.
When uploading a .pfx file with multiple certificates, RavenDB will add all of the certificates to the list of registered certificates as one entry and will allow access to all these certificates explicitly by their thumbprint.